The proliferation of powerful notebook computers and wireless communication promises to provide users with network access at any time and in any location.
Recent advances in hardware and communication technologies have introduced the era of mobile computing. The proliferation of powerful notebook computers and wireless communication promises to provide users with network access at any time and in any location. This continuous connectivity will allow users to be quickly notified of changing events and provide them with the resources necessary to respond to them even when in transit.
Unfortunately, present day Internetworking protocols like TCP/IP, IPX, and Appletalk behave awkwardly when dealing with host migration between networks.[footnote:In the Internet jargon, computers are often referred to as hosts.] Current versions of the Internet Protocol (IP) implicitly assume the point at which a computer attaches to the Internet is fixed, and its IP address identifies the network to which it is attached. Datagrams are sent to a computer based on the location information contained in its IP address.
If a mobile computer, or mobile host, moves to a new network while keeping its IP address unchanged, its address will not reflect the new point of attachment. Consequently, existing routing protocols will be unable to route datagrams to it correctly. In this situation, the mobile host must be reconfigured with a different IP address representative of its new location.
Not only is this process cumbersome for ordinary users, but it also presents the problem of informing potential correspondents of the new address. Furthermore, changing the IP address will cause already-established transport layer connections (for example, ftp or telnet sessions) to be lost. Put simply, under the current Internet Protocol, if the mobile host moves without changing its address, it will lose routing; but if it does change its address, it will lose connections.
Mobile-IP is an enhancement to IP which allows a computer to roam freely on the Internet while still maintaining the same IP address. The Internet Engineering Task Force (IETF) is currently developing a Mobile-IP standard which, at the time of this writing, is in its sixteenth revision. The Mobile-IP architecture, as proposed by the IETF, defines special entities called the Home Agent (HA) and Foreign Agent (FA) which cooperate to allow a Mobile Host (MH) to move without changing its IP address. The term mobility agent is used to refer to a computer acting as either a Home Agent, Foreign Agent, or both. A network is described as having mobility support if it is equipped with a mobility agent.
Each Mobile Host is associated with a unique home network as indicated by its permanent IP address. Normal IP routing always delivers packets meant for the MH to this network. When an MH is away, a specially designated computer on this network—its Home Agent—is responsible for intercepting and forwarding its packets.
The MH uses a special registration protocol to keep its HA informed of its current location. Whenever an MH moves from its home network to a foreign network or from one foreign network to another, it chooses a Foreign Agent on the new network and uses it to forward a registration message to its HA.
After a successful registration, packets arriving for the MH on its home network are encapsulated by its HA and sent to its FA. Encapsulation refers to the process of enclosing the original datagram as data inside another datagram with a new IP header. This is similar to the post office affixing a new address label over an older label when forwarding mail for a recipient who has moved. The source and destination address fields in the outer header correspond to the HA and FA, respectively. This mechanism is also called tunneling, since intermediate routers remain oblivious of the original inner-IP header. In the absence of this encapsulation, intermediate routers will simply return packets to the home network. On receiving the encapsulated datagram, the FA strips off the outer header and delivers the newly exposed datagram to the appropriate visiting MH on its local network.
Host movements typically cause some datagrams to be lost while routing tables at the HA and FA re-adjust to reflect the move. However, by using retransmissions and acknowledgments, connections maintained by the transport layer protocol are able to survive these losses in the same way they survive losses due to congestion. Note that even when the MH is away, datagrams meant for it are always sent first to its home network, in many cases resulting in a non-optimal route.
| Figure 1 | Figure 2 | Figure 3 |
 |
 |
 |
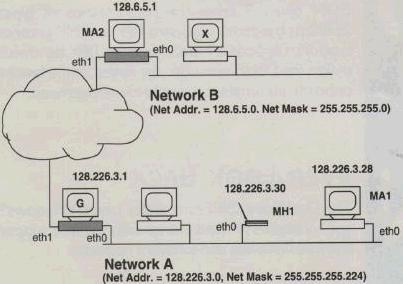
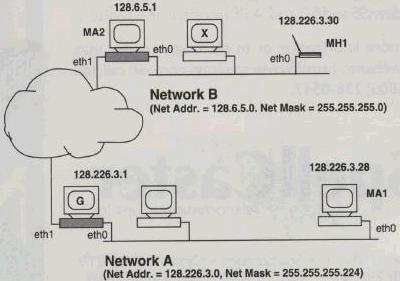
Figures 1 and Figure 2 show a mobility-supporting internetwork which serves as an illustrative example. It shows two mobility- supporting networks, Network A and Network B, which are equipped with mobility agents MA1 and MA2, respectively. A mobile host, MH1, is also shown, whose home network is Network A. Whenever MH1 is away, MA1 acts as its home agent. When MH1 visits Network B, MA2 acts as its foreign agent.
It is worth pointing out that changes introduced by Mobile-IP are independent of the communication medium in use. Even though this figure shows mobility support in a wired internetwork, the Mobile-IP works just as effectively in a wireless environment.
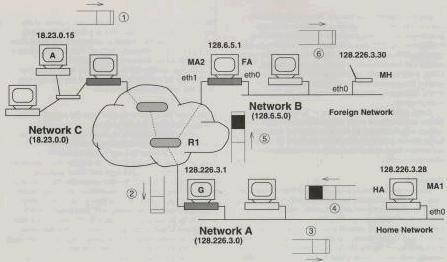
Figure 3 further illustrates the main idea behind Mobile-IP. It shows an IP datagram as it flows from computer A (IP address 18.23.0.15) to the mobile host (IP address 128.226.3.30). In this figure, the mobile host is shown to be away from its home network. Hosts MA1 (IP address 128.226.3.28) and MA2 (IP address 128.6.5.1) are acting as its home agent and foreign agent, respectively.
The IP header in the datagram, as it leaves A, indicates 128.226.3.30 as the destination. In Figure 3, this header is shown as the black portion of the datagram. Therefore, this datagram is routed to Network A (steps 1 and 2). Here, the home agent picks up the datagram and inserts an additional IP header before re-injecting it into the network (steps 3 and 4). The new IP header carries 128.6.5.1 as its destination address. This header is shown with cross hatched lines in Figure 3. As this is the header seen by intermediate routers like R1, the datagram is correctly routed to the foreign agent (step 5). By this time, the registration process has already informed the foreign agent of the mobile host’s presence on the local net. When the encapsulated datagram arrives at MA2, the outer header is stripped. The newly exposed header reveals the MH as the destination and the datagram is forwarded appropriately (step 6).
The IETF Mobile-IP draft also allows a Mobile Host to do its own decapsulation. In this case, the MH must acquire a temporary IP address on the foreign network (e.g., using DHCP) to be used for forwarding. This allows a mobile host to receive datagrams away from its home network even in the absence of a Foreign Agent. The downside of this approach is the kernel on the MH must now be modified to handle encapsulated datagrams.
The steady increase in the sales of portable computers is indicative of a growing base of mobile users. IETF’s proposed Mobile-IP standard will facilitate inter-operation between mobile devices designed by different vendors and further contribute to the popularization of mobile computing. Our research group at the State University of New York at Binghamton has developed a Mobile-IP implementation for Linux. This software and related documentation can be downloaded from the Linux Mobile-IP home page at http://anchor.cs.binghamton.edu/~mobileip/. The page also contains links to other Linux and portable computing resources.
All three authors are affiliated with the Department of Computer Science at the State University of New York, Binghamton. They can be reached at mobileip@anchor.cs.binghamton.edu.
 Linux, Linux OS, Free Linux Operating System, Linux India Linux, Linux OS,Free Linux Operating System,Linux India supports Linux users in India, Free Software on Linux OS, Linux India helps to growth Linux OS in India
Linux, Linux OS, Free Linux Operating System, Linux India Linux, Linux OS,Free Linux Operating System,Linux India supports Linux users in India, Free Software on Linux OS, Linux India helps to growth Linux OS in India



